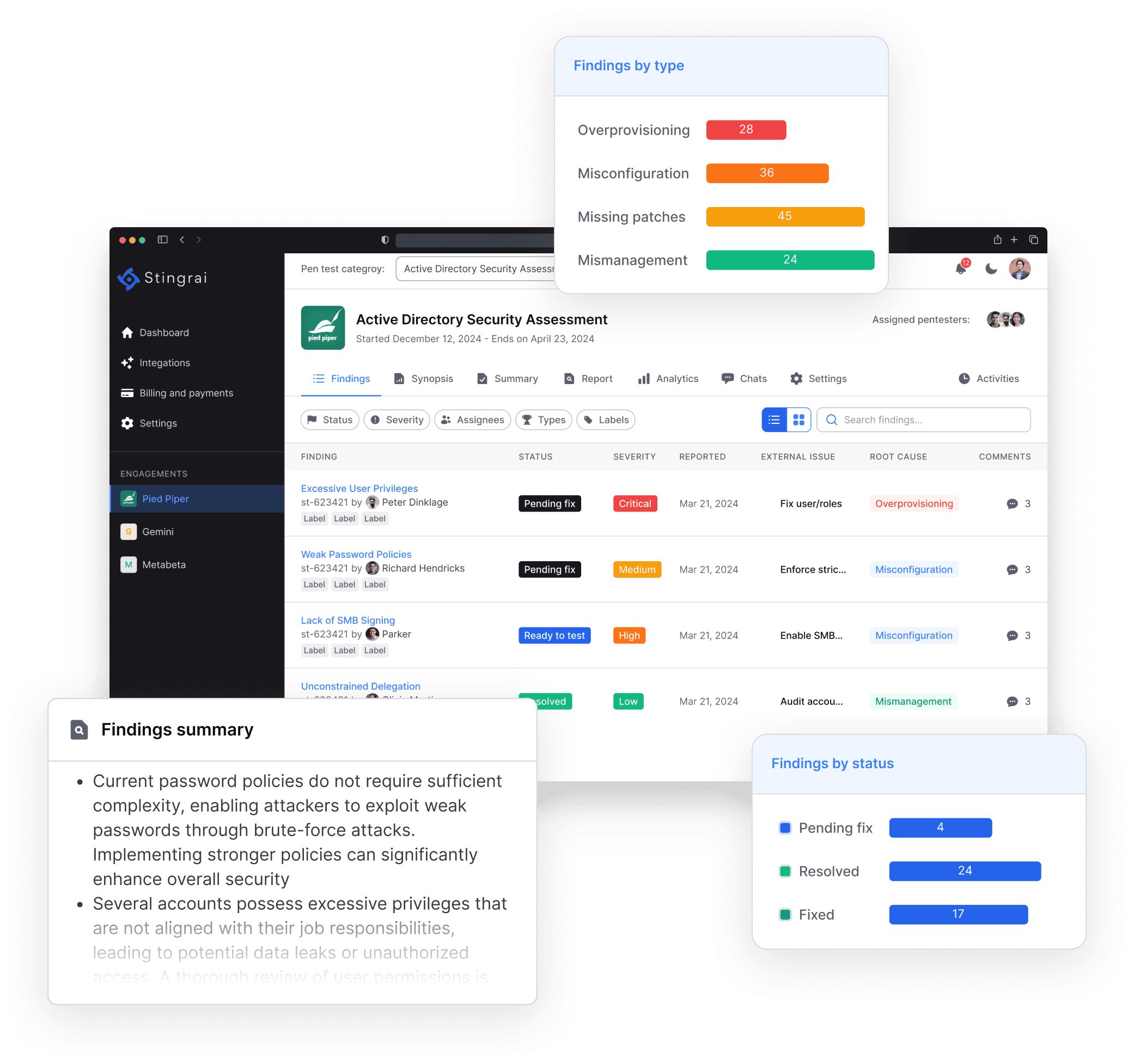
Identify and remediate critical vulnerabilities within your Active Directory environment. This assessment uncovers misconfigurations, excessive privileges, and attack paths to reduce risk and strengthen internal defenses.
Led by expert white-hat hackers and delivered through our Penetration Testing as a Service (PTaaS) platform.


Enhance the security of your Active Directory environment with our comprehensive assessment. Our engagement simulates real-world attack techniques to uncover and help remediate critical weaknesses such as:
Inactive user/computer accounts, legacy protocols, and outdated authentication protocols.
Misconfigured ACLs and delegation settings that could enable unauthorized account takeover.
Vulnerable domain trusts, including insecure SID history and inactive trust relationships.
Exploitable issues like golden ticket persistence, shadow admin accounts, and unauthorized password dumps.
Active Directory Security Assessment is designed to deliver actionable guidance for mitigating security risks in your Active Directory environment. It focuses on identifying misconfigurations, privilege escalation paths, nd weaknesses in the management of privileged accounts and groups, as well as assessing the integrity of domain and forest trusts. This assessment helps strengthen the overall security posture of your Active Directory environment.






Pingcastle
A high‑efficiency enterprise grade Active Directory assessment tool that uses a maturity‑based risk framework to quickly surface critical security gaps. It evaluates stale objects, weak delegation, insecure trusts, exposed ACLs, and privilege misuse—delivering visual dashboards, risk scores, and prioritized remediation guidance.

Bloodhound
An AD reconnaissance and attack‑path mapping platform favored by red teams. Using graph theory with data from SharpHound or AzureHound, it models relationships, discovers hidden privilege escalations, lateral movement paths, and misconfigurations enabling testers to plan targeted exploitation and prioritize remediation.
Innovative PTaaS Platform
Our Penetration Testing as a Service (PTaaS) model provides continuous, on-demand security testing, giving you real-time insights and proactive threat management. We focus on delivering measurable improvements, backed by detailed reports and recommendations.
Proven Track Record
We have a history of successfully securing businesses of all sizes, from startups to Fortune 500 companies. Don’t just take our word for it, read verified customer reviews about our work on Clutch.co.
Client-Centric Approach
We prioritize your needs and work closely with you throughout the process, offering clear communication, regular updates, and ongoing support.
Simulate Real Threats
At Stingrai, we don’t just run tests—we simulate real-world hacking scenarios to expose vulnerabilities before malicious actors can exploit them. By replicating the tactics, techniques, and procedures of real hackers, we identify critical weaknesses and show you exactly what needs to be fixed.
Expert Remediation Support
Stingrai offers detailed remediation steps along with free on-call support, ensuring our clients receive expert guidance to efficiently fix vulnerabilities and strengthen their security.
Accessible to All
We believe advanced security should be accessible to all. That’s why Stingrai offers competitive pricing without compromising on quality. Protect your organization with top-tier security assessments tailored to your budget.
Simulate real-world attacks with the expertise of our elite white-hat hackers. We identify vulnerabilities before they can be exploited, providing clear guidance on how to fix them through our cutting-edge platform, all at competitive pricing.

