Gustavo Roberto is a Team Lead Penetration Tester at Stingrai.io. As an expert in cybersecurity, he is here to share his experience on recovering a hacked account on X (formerly Twitter). He explains what likely happened, how the attacker acted, and, most importantly, how he reversed the situation.
It All Started on the Way to Jiu-Jitsu Training
While heading to his Jiu-Jitsu class, Gustavo received a call from a clearly panicked friend. The friend’s account on X had been hacked. The friend asked how an account that was "theoretically secure" could be taken over so easily.
Gustavo asked the basic questions:
Does he use two-factor authentication (2FA)? – No.
Is his password strong, with letters, numbers, and symbols? – Also no.
Does he change his password regularly? – Never.
Right away, Gustavo said: "That account isn’t secure at all, my friend."
The Likely Modus Operandi
Recently, there have been several password leaks. When that happens, bots automatically attempt to use those leaked credentials across popular services like X.
In the friend’s case, it appeared that one of those bots had successfully logged in, immediately changed the email and password, and taken full control of the account. The goal could range from spreading fake news to using the account as a "warehouse" for selling followers or boosting bot engagement.
The Key Piece for the Recovery
During the conversation, the friend mentioned he had received a strange email and showed Gustavo a screenshot. That small detail was crucial for Gustavo to understand what had happened and reverse the attack.
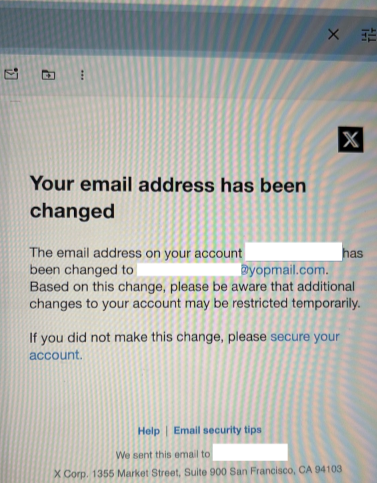
By analyzing the sender, Gustavo noticed that the attacker had used a service called Yopmail, a temporary and anonymous email provider popular among scammers. These emails require no registration, are disposable, and are supposed to "expire" after a while.
But here’s the catch: the email doesn’t actually disappear. Just type the same address again on the Yopmail website and there it is, with all previous messages still accessible. That’s exactly what Gustavo did.
PoC | Creating an Email on Yopmail
Below, it is demonstrated how easy it is to create an email on Yopmail.
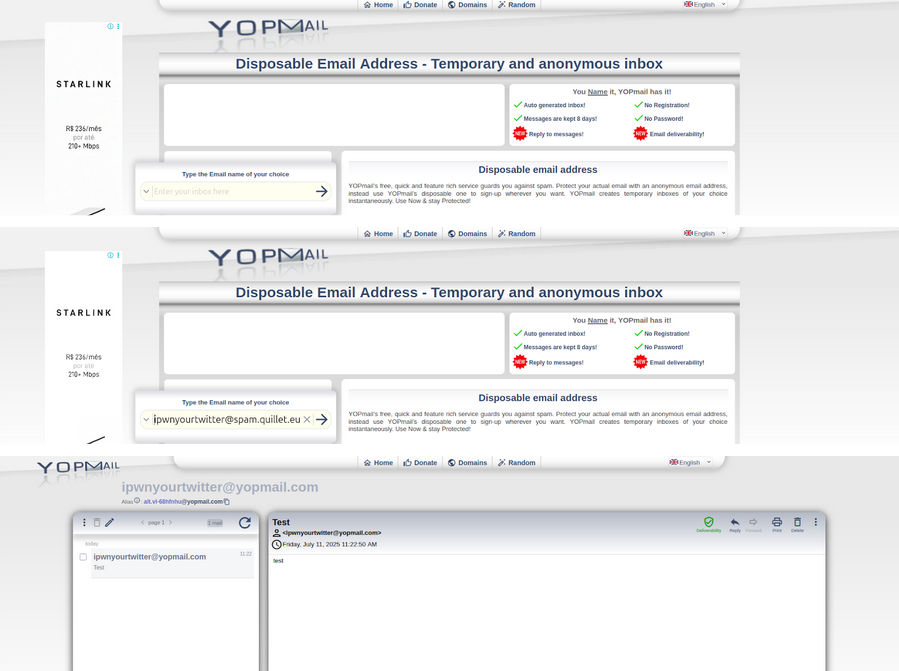
In fact, if one accesses this inbox from their own machine, they’ll find a test message left there by Gustavo.
Access Restored
With access to the attacker’s inbox, Gustavo and his friend intercepted the password reset email. They used the code from it to regain control of the account.
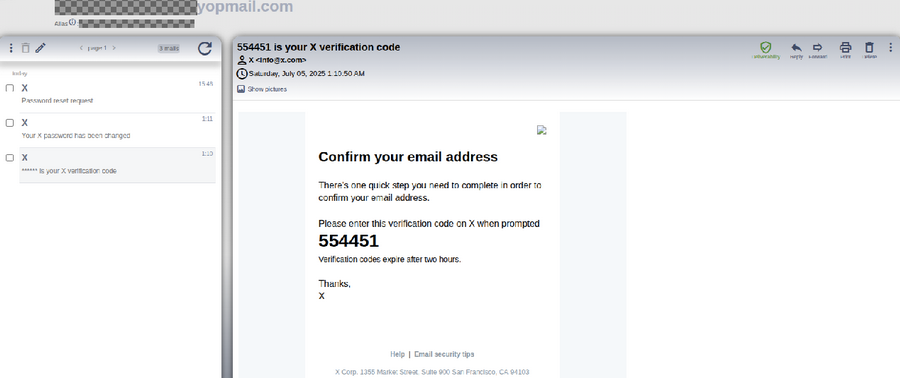
Immediately after, they checked the login history. The unauthorized access originated from a VPN exit node in Germany, a common tactic used by attackers to conceal their real location.
More Surprises Along the Way
Even after regaining access, there was still an issue: X's platform was generating errors when attempting to change the password or enable 2FA. On mobile, the account functioned properly, but on the browser, it was unresponsive.
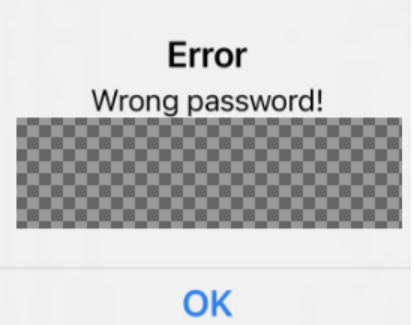
Each attempt to make a change resulted in a different error message.
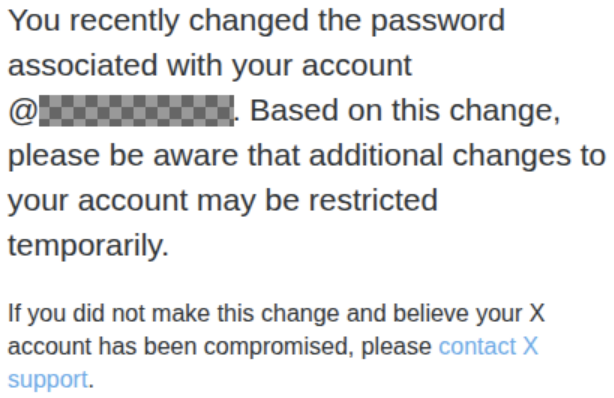
While waiting for the system to stabilize, Gustavo recommended that his friend interact with the platform by liking posts, publishing content, and joining groups. This would help establish legitimate activity, in case they needed to prove account ownership later.
Fortunately, after some time, a new, more promising message from X appeared.
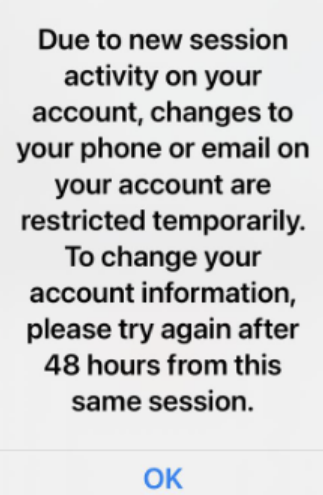
With patience and persistence, they were able to reconfigure everything, activate 2FA, and secure the account once and for all.
Lessons Learned
This experience taught Gustavo's friend several valuable lessons, which he hopes will also benefit the readers:
Always use two-factor authentication (2FA): Even if someone obtains your password, they still won’t be able to log in.
Avoid weak or reused passwords: Utilize a password manager and create unique combinations for each service.
Be cautious of services like Yopmail: If you receive email change notifications from these domains, be immediately suspicious.
Don’t panic: With the right information and some investigation, it’s often possible to reverse many incidents.
Gustavo hopes this story was helpful and assists readers in better protecting their own accounts.

